|
||||
|
Computer Repair San antonio-New Year’s Resolutions for Your Computer
|
||||
|
Computer Repair San Antonio-More Than A Virus, Common Malware to Watch Out For
|
||||
|
Don’t unplug your Computer to Shut It Down!-Computer Repair San Antonio
Can I Just Unplug My Computer to Shut It Down?
You may damage your computer.
By pulling the plug or forcing a power-off by holding down the power button, you risk corrupting data on your hard drive and damaging hardware.
I’m not sure what kinds of problems you’re having with the power button, but even that needs to be used correctly, or you could end up with the very problems you’re seeing.
HP Recalls Batteries for Notebook Computers and Mobile Workstations Due to Fire and Burn Hazards-Computer Repair San Antonio
HP Recalls Batteries for Notebook Computers and Mobile Workstations Due to Fire and Burn Hazards
HP toll-free at 888-202-4320 from 8 a.m. to 7 p.m. CT Monday through Friday or online at www.HP.com/go/batteryprogram2018 or www.hp.com and click “Recalls” for more information.
This recall involves lithium-ion batteries for HP Notebook computers and mobile workstations. The batteries were shipped with or sold as accessories for HP ProBooks (64x G2 and G3 series, 65x G2 and G3 series), HPx360 310 G2, HP Envy m6, HP Pavilion x360, HP 11, HP ZBook (17 G3, 17 G4, and Studio G3) Mobile Workstations. The batteries were also sold as accessories or replacement batteries for the HP ZBook Studio G4 mobile workstation or for any of the products listed above.
Consumers should immediately visit www.HP.com/go/batteryprogram2018 to see if their battery is included in the recall and for instructions on how to enable “Battery Safety Mode” if their battery is included in the recall. The website provides consumers instructions on how to initiate the validation utility to check their battery and what to download if their battery is included in the recall. These batteries are not customer-replaceable. HP will provide free battery replacement services by an authorized technician.
HP has received eight reports of battery packs overheating, melting, or charring, including three reports of property damage totaling $4,500 with one report of a minor injury involving a first degree burn to the hand.
Best Buy and other stores and authorized dealers nationwide and online at www.Amazon.com, www.hp.com and other websites. The batteries were shipped in notebook computers and mobile workstations sold from December 2015 through December 2017 for between $300 and $4,000. The batteries were also sold separately for between $50 and $90.
HP Inc., of Palo Alto, Calif.
Windows Meltdown-Spectre fix: How to check if your AV is blocking Microsoft patch SAPC Upgrades
Windows Meltdown-Spectre fix: How to check if your AV is blocking Microsoft patch
Antivirus firms are gradually adding support for Microsoft’s Windows patch for the Meltdown and Spectre attack methods that affect most modern CPUs.
As Microsoft warned this week, it’s not delivering its January 3 Windows security updates to customers if they’re running third-party antivirus, unless the AV is confirmed to be compatible with it.
Microsoft’s testing found some antivirus products were producing errors by making unsupported calls into Windows kernel memory, resulting in blue screen of death (BSOD) errors.
Third-party Windows antivirus products need to support Microsoft’s security update and set a Windows registry key for customers to receive the update via Windows Update.
To make matters more confusing, only some antivirus vendors are actually doing both, while others require admins to set the registry key themselves, using Microsoft’s instructions. Additionally, some antivirus companies haven’t completed compatibility testing.
Microsoft hasn’t said which antivirus products are compatible beyond its own Windows Defender and Microsoft Security Essentials. However, security researcher Kevin Beaumont has created a public spreadsheet that may help IT admins prepare for installing Microsoft’s mitigations for the attack techniques that affect CPUs from Intel, AMD and Arm, albeit to differing degrees.

Call 210-549-6477 with questions
Laptop Repair in San Antonio Texas-SAPC Upgrades
If you are looking for the best Laptop Repair in San Antonio Texas and surrounding areas like Live Oak, Converse, Windcrest, Selma and Schertz consider SAPC Upgrades for affordable fair priced Laptop Repair
- Protecting your DATA is our #1 goal
- Fair Flat Rate in shop pricing
- Free Estimates
- Malwarebytes Authorized Reseller
- Friendly, honest communication, no “geek-speak”
- Professional, experienced technician
- Microsoft Registered Partner
- Locally owned and operated since 2003
- We strive to build lasting relationships with our customers
SAPC Upgrades offers many quality computer repair services.
- LCD Repair
- Laptop Repair
- Fast Support
- Honest Estimates
- Virus Removal
- Attention To Detail
- Malware Removal
- Data Backup
- Trojan Removal
Computer Repair San Antonio, Texas-SAPC Upgrades
Computer Repair in San Antonio-SAPC Upgrades
If you are looking for the best Computer Repair in San Antonio Texas and surrounding areas like Live Oak, Converse, Windcrest, Selma and Schertz consider SAPC Upgrades for affordable fair priced Computer Repair.
- Protecting your DATA is our #1 goal
- Fair Flat Rate in shop/remote pricing
- Free Estimates
- Malwarebytes Authorized Reseller
- Friendly, honest communication, no “geek-speak”
- Professional, experienced technician
- Microsoft Registered Partner
- Locally owned and operated since 2003
- We strive to build lasting relationships with our customers
SAPC Upgrades offers many quality computer repair services.

We Service
- LCD Repair
- Laptop Repair
- Fast Support
- Honest Estimates
- Virus Removal
- Attention To Detail
- Malware Removal
- Data Backup
- Trojan Removal
- North East San Antonio
All You Need to Know About the WannaCrypt Ransomware
WannaCrypt is a ransomware program targeting Windows. On Friday, 12 May 2017, a large cyber-attack using it was launched, infecting more than 230,000 computers in 150 countries, demanding ransom payments in the cryptocurrency bitcoin in 28 languages.
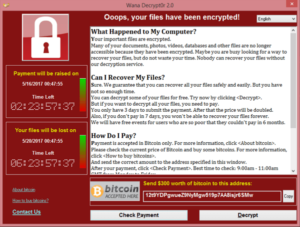
It was being spread primarily by phishing emails (most commonly links or attachments) and as a worm on unpatched systems.
The attack affected Telefónica and several other large companies in Spain, as well as parts of Britain’s National Health Service, FedEx, Deutsche Bahn and LATAM Airlines. Other targets in at least 99 countries were also reported to have been attacked around the same time.
WannaCry is believed to use the EternalBlue exploit, which was developed by the U.S. National Security Agency (NSA) to attack computers running Microsoft Windows operating systems. Although a patch to remove the underlying vulnerability for supported systems (Windows Vista and later operating systems) had been issued on 14 March 2017, delays in applying security updates and lack of support by Microsoft of legacy versions of Windows left many users vulnerable. Due to the scale of the attack, to deal with the unsupported Windows systems and to contain the spread of the ransomware, Microsoft has taken the unusual step of releasing updates for all older unsupported operating systems from Windows XP onwards.
Shortly after the attack began, a researcher found an effective kill switch, which prevented many new infections and allowed time to patch systems. This significantly slowed the spread. It was later reported that new versions that lack the kill switch were detected. Cyber security experts also warn of a second wave of the attack due to such variants and the beginning of the new workweek.
As always, be sure your Windows is up to date. XP users should consider upgrading where possible. The vulnerabilities for that operating system will not go away. Don’t click links in an email. Don’t open file attachments.
And, our longest running advice; back up regularly. You can back up to the cloud, or another drive. Programs like Macrium Reflect can Image your drive essentially restoring everything at any time.
Animated Map of How Tens of Thousands of Computers Were Infected With Ransomware
https://www.nytimes.com/interactive/2017/05/12/world/europe/wannacry-ransomware-map.html